The Ultimate Guide to Data Key Management Services (DKMS) for Enhanced Cloud Security is the need of the hour to prevent data breaches and maintain compliance.
Editor's Notes: The Ultimate Guide to Data Key Management Services (DKMS) for Enhanced Cloud Security has published on 22nd February 2023. As cloud adoption becomes more and more widespread, data security becomes more important. DKMS is a cloud service that helps organizations manage the encryption keys used to protect their data, and it's an essential tool for protecting sensitive data in the cloud.
After doing some analysis, digging out information, and thorough research, we have put together this guide to help you make the right decision.
Key differences or Key takeaways
| DKMS | Other Key Management Solutions | |
|---|---|---|
| Scalability | Highly scalable, can manage keys for millions of objects | May not be able to handle large-scale deployments |
| Security | Uses strong encryption algorithms and access controls | May not provide the same level of security |
| Compliance | Helps organizations meet compliance requirements | May not be compliant with all regulations |
| Cost | Can be expensive, but may be worth the investment for organizations with sensitive data | May be less expensive, but may not provide the same features and benefits |
Transition to main article topics
- What is DKMS?
- How does DKMS work?
- Benefits of using DKMS
- How to choose the right DKMS provider
- Best practices for using DKMS
FAQ
This FAQ section provides answers to some commonly asked questions regarding Data Key Management Services (DKMS) for enhanced cloud security as discussed in The Ultimate Guide To Data Key Management Services (DKMS) For Enhanced Cloud Security.
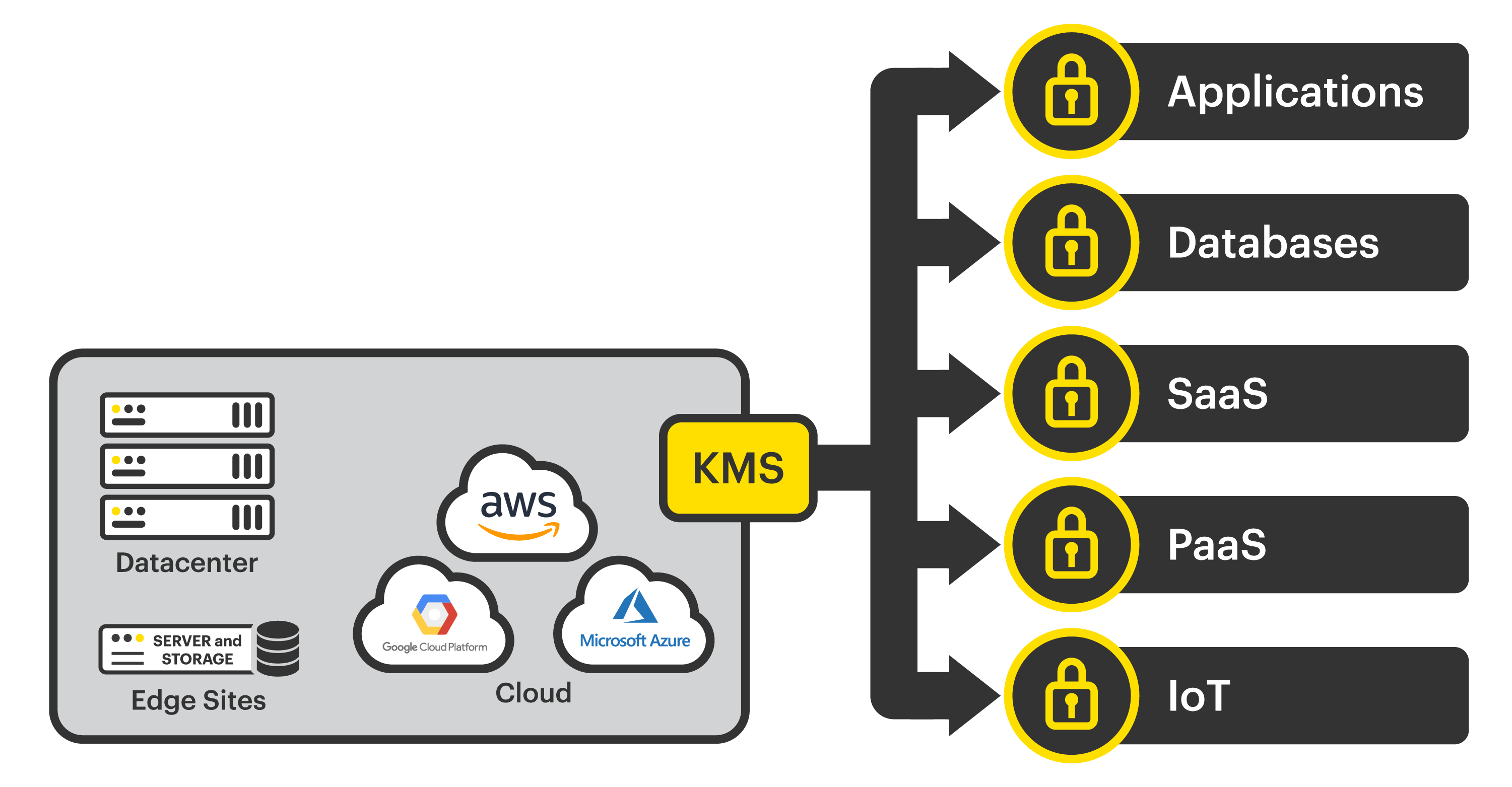
Key Management - A Beginners Guide - StorMagic SvSAN - Source stormagic.com
Question 1: What are the benefits of using a DKMS?
A DKMS centralizes and manages encryption keys, providing several advantages. It simplifies key management, enhances security by reducing the risk of key compromise, and helps maintain compliance with regulatory requirements.
Question 2: How does a DKMS integrate with cloud services?
A DKMS integrates with cloud services through APIs or SDKs. This integration allows the DKMS to manage and protect encryption keys used by cloud services, ensuring secure data encryption and decryption.
Question 3: What are the different types of DKMS?
There are various types of DKMS, including cloud-based DKMS, on-premises DKMS, and hybrid DKMS. Each type offers different features and deployment options, allowing organizations to choose the most suitable solution for their needs.
Question 4: How can a DKMS improve cloud security?
A DKMS strengthens cloud security by centralizing encryption key management. It reduces the risk of unauthorized access to encryption keys, preventing data breaches and ensuring the confidentiality and integrity of sensitive data.
Question 5: What are the best practices for using a DKMS?
Best practices for using a DKMS include defining clear key management policies, regularly rotating encryption keys, implementing strong access controls, and conducting regular security audits to ensure the ongoing effectiveness of the DKMS.
Question 6: How can organizations get started with a DKMS?
Organizations can begin using a DKMS by evaluating their key management needs, choosing a suitable DKMS solution, and integrating it with their cloud services. It is recommended to consult with experts or refer to vendor documentation for guidance throughout the implementation process.
By addressing these common questions, this FAQ section aims to provide a deeper understanding of DKMS and its role in enhancing cloud security.
Tips for Enhanced Cloud Security with Data Key Management Services (DKMS)
Implementing Data Key Management Services (DKMS) can significantly bolster cloud security. Here are some key tips to maximize its effectiveness:
Tip 1: Centralize Key Management
Consolidate all encryption keys under a centralized DKMS, allowing for consistent key management policies and simplified key rotation.
Tip 2: Use Strong Encryption Algorithms
Employ robust encryption algorithms like AES-256 to safeguard sensitive data at rest and in transit, ensuring its confidentiality.
Tip 3: Implement Multi-Factor Authentication (MFA)
Enhance security by requiring multiple forms of authentication, such as a password and a one-time code, to access keys and encrypted data.
Tip 4: Monitor and Audit Key Usage
Establish monitoring systems to track key utilization, detect anomalous activity, and ensure compliance with security policies.
Tip 5: Regularly Rotate Keys
Periodically update encryption keys to minimize the risk of compromise, ensuring that data remains protected against evolving threats.
Tip 6: Leverage Hardware Security Modules (HSMs)
Integrate HSMs to provide tamper-resistant storage for encryption keys, ensuring their integrity and protection from unauthorized access.
Tip 7: Enforce Key Management Policies
Establish clear and comprehensive key management policies to govern key creation, rotation, usage, and deletion, ensuring consistent security practices.
Summary: Implementing DKMS with these tips empowers organizations to enhance cloud security by centralizing key management, utilizing strong encryption, enforcing authentication, monitoring key usage, rotating keys regularly, leveraging HSMs, and adhering to well-defined policies. This multifaceted approach ensures the confidentiality, integrity, and availability of sensitive data in the cloud.
The Ultimate Guide To Data Key Management Services (DKMS) For Enhanced Cloud Security
In the realm of cloud security, safeguarding data has become paramount. Data Key Management Services (DKMS) stand as a cornerstone for achieving this goal, providing secure and efficient management of encryption keys. This guide explores six key aspects that define the role of DKMS in strengthening cloud security:
- Centralized Control: DKMS provides a single point of control for key generation, storage, and distribution, ensuring consistent security policies across all cloud platforms.
- Granular Access: It enables the assignment of specific roles and permissions to users, allowing for fine-grained access to data and keys, minimizing risk.
- Auditability and Compliance: DKMS maintains detailed audit logs, facilitating security audits and compliance with regulatory requirements.
- High Availability: By replicating keys across multiple zones, DKMS ensures continuous availability of encryption keys, preventing data loss or outages.
- Integration with Cloud Services: It seamlessly integrates with major cloud providers, allowing for easy management of keys used by various cloud services.
- Cost Optimization: DKMS can reduce infrastructure costs by eliminating the need for dedicated hardware or software for key management.
These key aspects collectively empower organizations to protect their sensitive data in the cloud, ensuring confidentiality, integrity, and regulatory compliance. DKMS serves as a critical component in the cloud security arsenal, enabling enterprises to embrace cloud computing with confidence.
在Fedora上安装NVIDIA驱动详细教程及解析_fedora nvidia-CSDN博客 - Source blog.csdn.net
The Ultimate Guide To Data Key Management Services (DKMS) For Enhanced Cloud Security
In the realm of cloud computing, ensuring the confidentiality and integrity of sensitive data is paramount. Data Key Management Services (DKMS) emerge as indispensable tools for achieving this objective by providing secure storage, management, and distribution of encryption keys. This guide delves into the intricacies of DKMS, empowering readers to harness its capabilities for enhanced cloud security.

WIRD DPoD - Data Protection on Demand Services - Source www.wirdgroup.com
As organizations migrate their data and applications to the cloud, they encounter the challenge of managing encryption keys effectively. DKMS offers a centralized and secure solution for key generation, storage, and rotation, ensuring that only authorized entities have access to sensitive data. By leveraging DKMS, organizations can simplify key management tasks, reduce operational overhead, and enhance their overall security posture.
Practical examples abound, showcasing the real-world impact of DKMS. In the healthcare industry, DKMS enables secure storage and sharing of patient records, ensuring compliance with stringent regulations and protecting patient privacy. In the financial sector, DKMS safeguards sensitive financial data, minimizing the risk of unauthorized access and fraud.
Understanding the connection between DKMS and cloud security is crucial for organizations seeking to protect their valuable data assets. DKMS provides a robust framework for key management, eliminating the need for manual processes and reducing the risk of human error. It empowers organizations to implement robust access controls, audit key usage, and respond swiftly to security incidents.
In conclusion, the integration of DKMS into cloud security strategies is a transformative step towards safeguarding sensitive data. By centralizing key management, organizations streamline operations, enhance security, and ensure compliance with regulatory requirements. The insights provided in this guide empower readers to make informed decisions and implement DKMS effectively, ultimately safeguarding their data in the ever-evolving cloud landscape.
